Spreadsheets are a familiar tool, but when it comes to storing confidential supplier information, they can be a ticking time bomb. Let’s face it, spreadsheets were never designed for robust data security. Relying on them for supplier information puts you at risk of data breaches and unauthorized access. It potentially leads to a domino effect of legal and financial repercussions.
The Spreadsheet Achilles Heel: Vulnerability Everywhere
Spreadsheets are inherently vulnerable. Here’s why:
Weak Passwords: Many users rely on weak passwords to protect their spreadsheets, making them easy targets for hackers.
Accidental Sharing: A single misstep, like accidentally sending a spreadsheet with sensitive supplier data to the wrong recipient, can have disastrous consequences.
Limited Access Controls: Spreadsheets offer minimal control over who can access and modify data. A disgruntled employee or a curious colleague could easily view or even alter confidential information.
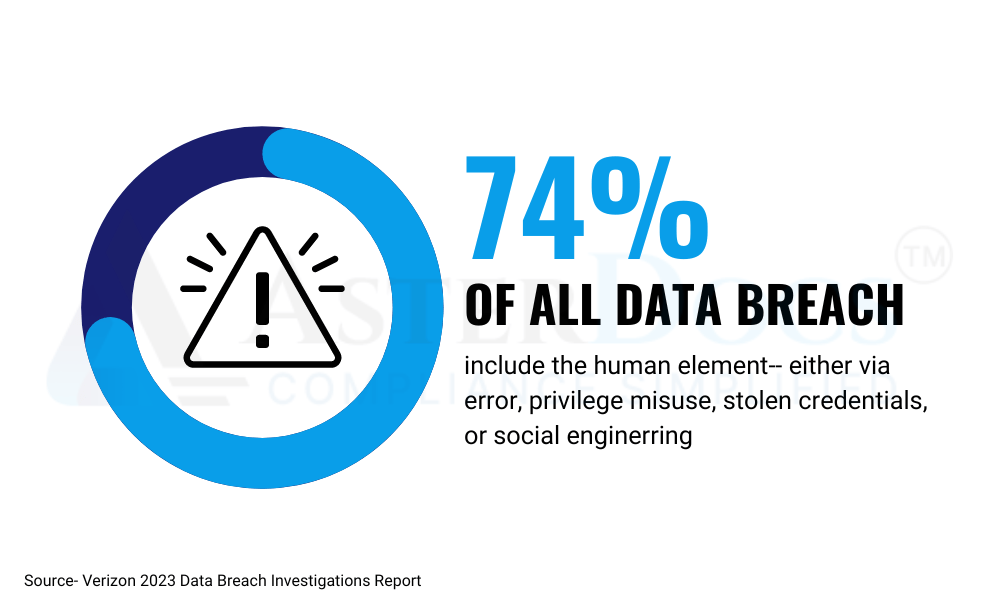
These vulnerabilities can lead to data breaches. Thus, exposing your suppliers’ sensitive information, such as contact details, financial data, and intellectual property.
The High Price of a Data Leak:
The consequences of a data breach involving supplier information can be severe:
Legal Ramifications: Depending on the nature of the data leaked, you could face hefty fines and legal action from both your suppliers and regulatory bodies.
Financial Loss: Breaches can damage your reputation and erode supplier trust, leading to lost business opportunities and potential customer churn.
Reputational Damage: A public data leak can severely tarnish your brand image, making it difficult to attract new suppliers and partners.
Security You Can Trust: Why Software is the Answer
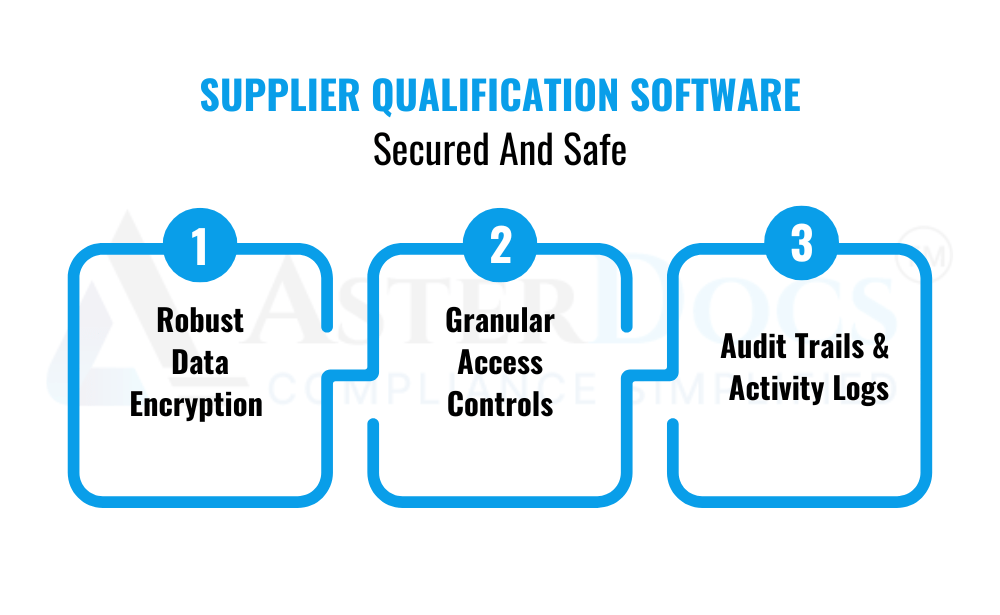
Supplier qualification software offers a secure and reliable alternative to spreadsheets. Here’s how it protects your data:
Robust Data Encryption: Data is encrypted at rest and in transit, ensuring it remains unreadable even if intercepted.
Granular Access Controls: You can define user permissions, restricting access to sensitive information only to authorized personnel.
Audit Trails and Activity Logs: Track every action taken within the software, providing clear visibility into who accessed what information and when.
By investing in dedicated supplier qualification software like AsterDocs you gain complete peace of mind knowing your confidential supplier information is safeguarded with the highest security standards.
Schedule A Demo
Don’t gamble with your suppliers’ trust and your company’s reputation. Move beyond spreadsheets and embrace a secure solution that protects your data and keeps your business thriving.