In today’s fast-paced business environment, email remains a crucial communication tool. However, when it comes to sharing sensitive documents, email can be a security liability. This blog dives into the hidden dangers lurking behind the seemingly convenient practice of emailing documents and explores secure alternatives offered by Asterdocs, a comprehensive document management system (DMS).
The Inherent Flaws of Email Security
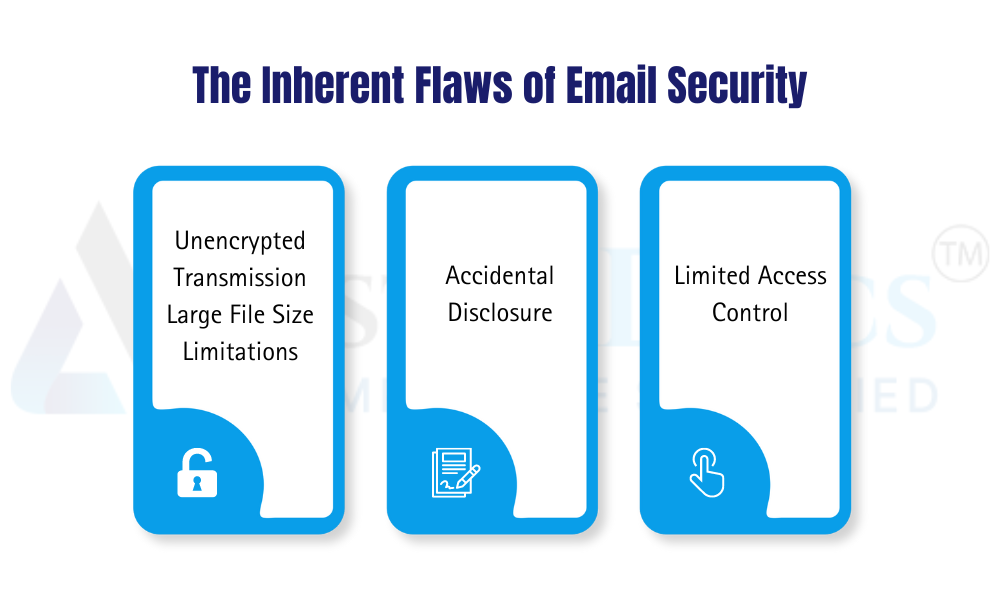
While email offers a seemingly quick and easy way to share documents, its inherent limitations pose significant security risks:
-
Unencrypted Transmission: Email messages travel through unencrypted channels, making them vulnerable to interception by hackers. Imagine you’re sending a confidential contract or sensitive financial data. Without encryption, anyone with access to the data stream could potentially steal this information, leading to data breaches, financial losses, and reputational damage for your business.
-
Large File Size Limitations: Many email providers restrict attachment sizes, often falling short of the needs of modern businesses. Large design files, engineering schematics, or high-resolution images may exceed these limitations. Splitting files into smaller chunks for email transmission creates a tangled mess. You risk losing parts of the information during transmission, compromising data integrity and overall security.
-
Accidental Disclosure: A single typo in an email address can have disastrous consequences. A misplaced keystroke could inadvertently send your confidential documents to the wrong recipient, exposing sensitive information to unauthorized individuals. This can lead to breaches of privacy, intellectual property theft, or even legal ramifications depending on the nature of the data.
-
Limited Access Control: Once you hit “send,” you relinquish a significant degree of control over who can access your documents. Emails can be easily forwarded or replied to, potentially spreading sensitive information beyond your intended recipient. Imagine sending a document to a colleague, only to have it forwarded to a competitor or unauthorized third party. This lack of granular access control can compromise confidentiality and data security.
Beyond Email: Exploring Secure Alternatives
Fortunately, secure alternatives exist to mitigate the risks associated with emailing documents. Here’s a breakdown of some options and their limitations:
-
Cloud Storage Platforms: Cloud storage services like Dropbox or Google Drive offer secure document storage with features like password protection and access controls. However, these platforms might not be ideal for highly sensitive information. User permissions and audit trails might be limited, making it difficult to track document access and ensure compliance with data privacy regulations.
-
File Transfer Services: Platforms designed for secure file transfer offer a more secure alternative than email. These services often encrypt data in transit and at rest, along with password protection for added security. However, they may lack functionalities like version control and audit trails, which are crucial for regulatory compliance and ensuring document integrity.
Asterdocs: A Comprehensive Solution for Secure Document Management
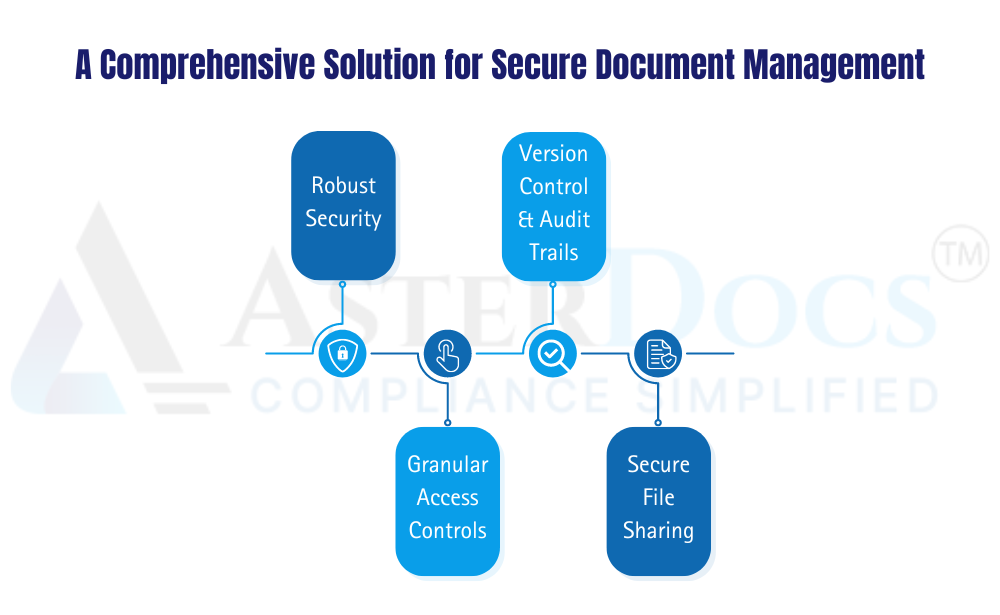
Asterdocs, a comprehensive document management system (DMS), offers a holistic solution for secure document sharing and management. It goes beyond simple storage by providing robust features designed to safeguard your sensitive information:
-
Robust Security: Asterdocs utilizes bank-grade encryption to protect your documents at rest and in transit. Think of it as a digital vault, ensuring only authorized users can access your confidential information.
-
Granular Access Controls: Define user permissions and access levels within Asterdocs. Grant specific individuals read-only access, edit permissions, or complete denial of access based on the document’s sensitivity and user roles. This ensures sensitive documents are only accessible to authorized personnel, minimizing the risk of unauthorized access and data breaches.
-
Version Control & Audit Trails: Track document revisions and user activity within Asterdocs. Maintain a clear audit trail for compliance purposes. Imagine needing to demonstrate that you’ve complied with a specific regulation. Asterdocs’ audit trails provide a detailed record of document changes and user actions, simplifying compliance audits and mitigating legal risks.
-
Secure File Sharing: Share documents securely with both internal and external collaborators using built-in features or integrations with third-party tools. Asterdocs allows you to set expiry dates on shared documents, request additional authentication from recipients, and even revoke access at any time. This level of control ensures your confidential information remains secure, even when collaborating with external parties.
Conclusion: Embrace Security & Efficiency with Asterdocs
While email might seem like a familiar and convenient option, the potential security risks are simply too great to ignore. Secure alternatives like Asterdocs’ document management system provide a safer and more reliable way to share sensitive information. Asterdocs empowers businesses of all sizes to manage and share documents with confidence, ensuring data security, regulatory compliance, and seamless collaboration.
Don’t gamble with the security of your sensitive information. Embrace a secure and efficient document management solution. Contact Asterdocs today to learn more about how we can help your business!