In today’s fast-paced business environment, email remains a primary communication tool. However, sharing sensitive documents via email can expose your business to a multitude of security risks. This blog delves into the potential security vulnerabilities associated with email and explores how Asterdocs, offers a secure and reliable alternative for document sharing.
The Hidden Risks of Emailing Sensitive Documents
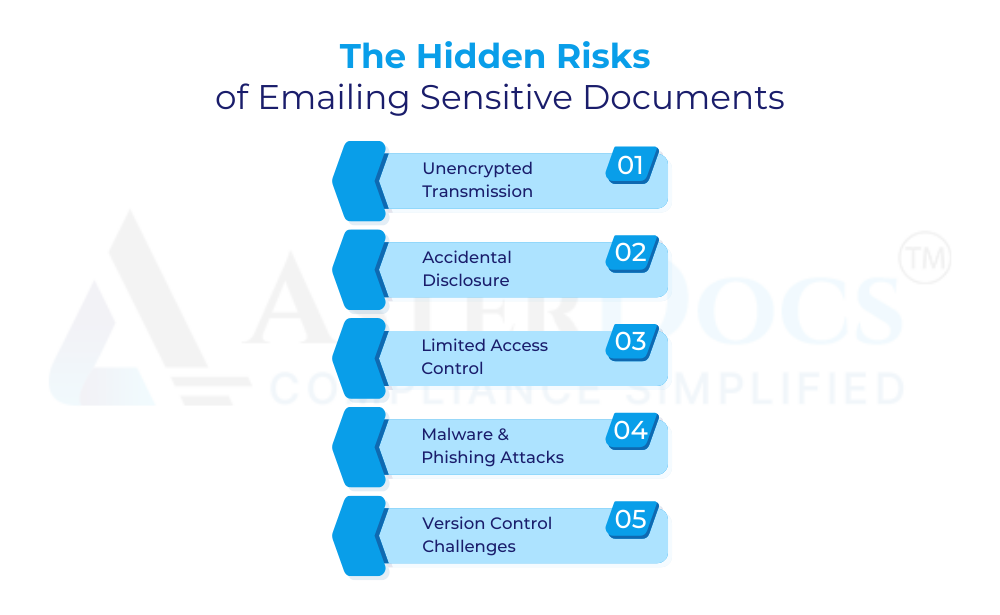
While email appears convenient, it lacks the security features essential for protecting sensitive documents. Here’s why email poses a security risk:
-
Unencrypted Transmission: Emails travel across unsecured networks, making them vulnerable to interception by unauthorized individuals. Sensitive information within attachments could be easily compromised.
-
Accidental Disclosure: A simple typo in the recipient address can lead to accidentally sending confidential documents to the wrong person.
-
Limited Access Control: Email offers minimal control over who can access shared documents once they are sent. Forwarded emails can quickly spread beyond intended recipients.
-
Malware & Phishing Attacks: Emails can be used as a gateway for malware and phishing attacks. Malicious attachments or links can compromise recipient systems and steal sensitive data.
-
Version Control Challenges: Emailing documents often creates multiple versions circulating simultaneously, leading to confusion and potential security breaches.
The Consequences of Email-Based Document Sharing
The security vulnerabilities associated with emailing sensitive documents can have serious consequences for your business:
-
Data Breaches & Financial Losses: Exposure of sensitive information, like customer data or financial records, can lead to costly data breaches and regulatory fines.
-
Reputational Damage: News of a security breach can severely damage your brand reputation and erode customer trust.
-
Compliance Violations: Failure to adequately protect sensitive data can lead to non-compliance with industry regulations and legal repercussions.
-
Loss of Competitive Advantage: Compromised confidential information can give competitors an unfair advantage in the marketplace.
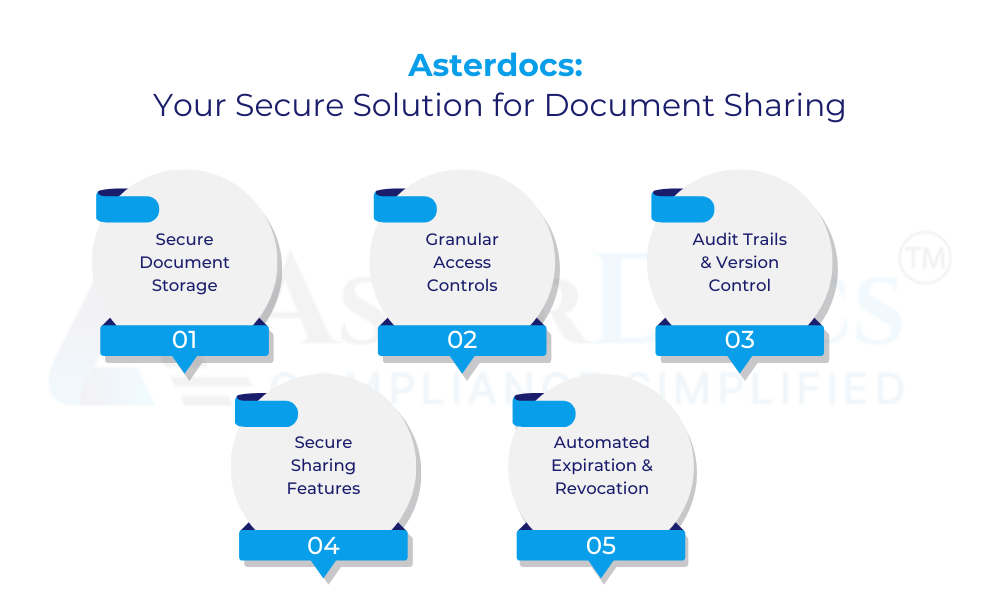
Asterdocs offers a robust document management system that addresses the security vulnerabilities of email-based document sharing:
-
Secure Document Storage: Store all sensitive documents in a centralized, secure repository with robust encryption to safeguard confidential information.
-
Granular Access Controls: Define user permissions and access levels, ensuring only authorized personnel can view, edit, or download specific documents.
-
Audit Trails & Version Control: Maintain a clear audit trail for all document activity, tracking access and modifications, and ensuring you always have the latest version readily available.
-
Secure Sharing Features: Share documents securely with internal and external users through a dedicated platform with permission controls and password protection.
-
Automated Expiration & Revocation: Set documents to automatically expire after a specific timeframe, or revoke access remotely if necessary, minimizing security risks.
Conclusion: Embrace Secure Document Sharing for Peace of Mind
By transitioning from email to Asterdocs, businesses can achieve secure document sharing and gain peace of mind:
-
Enhanced security for sensitive information.
-
Reduced risk of data breaches and compliance violations.
-
Improved collaboration and communication with internal and external stakeholders.
-
Streamlined document management and increased efficiency.
In today’s digital age, secure document sharing is no longer a luxury; it’s a necessity. Asterdocs empowers businesses to share documents with confidence, safeguarding information and building trust with partners and clients.