Developing a strong risk management framework for information systems is more important than ever in the current digital era. Given the ever-increasing stakes and the constant evolution of cyber threats, it is imperative to comprehend and mitigate risks. So, how can you ensure that your information systems are secure? Now let us explore the key elements of developing a robust risk management system.
Importance of Risk Management in Information Systems
Firstly, why is risk management so important for information systems? Well, without a solid risk management framework, your information systems are vulnerable to a myriad of threats. These threats can range from data breaches to system failures, each with the potential to disrupt operations, incur financial losses, and damage reputations. Consequently, implementing a robust risk management strategy is fundamental to safeguarding your organization’s critical assets.
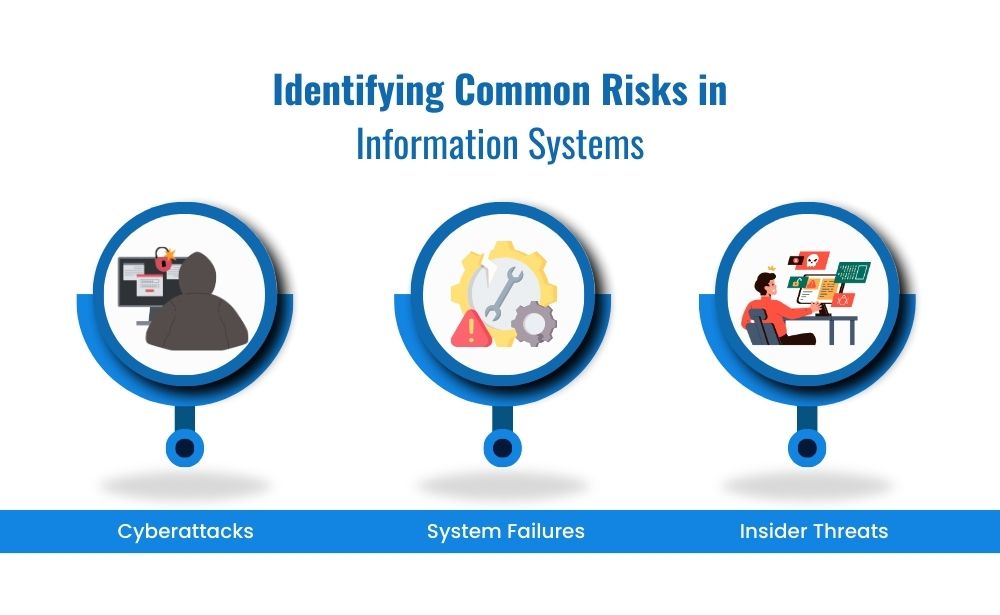
Identifying Risks in Information Systems
Next, identifying risks is the cornerstone of any risk management framework. But, what are the common risks in information systems? Cyberattacks, such as phishing and ransomware, are frequent culprits. Additionally, system downtimes due to hardware failures or software bugs can cause significant disruptions. Moreover, insider threats, whether intentional or accidental, can compromise data integrity. Each of these risks carries its own set of impacts, including data loss, operational downtime, and compliance issues.
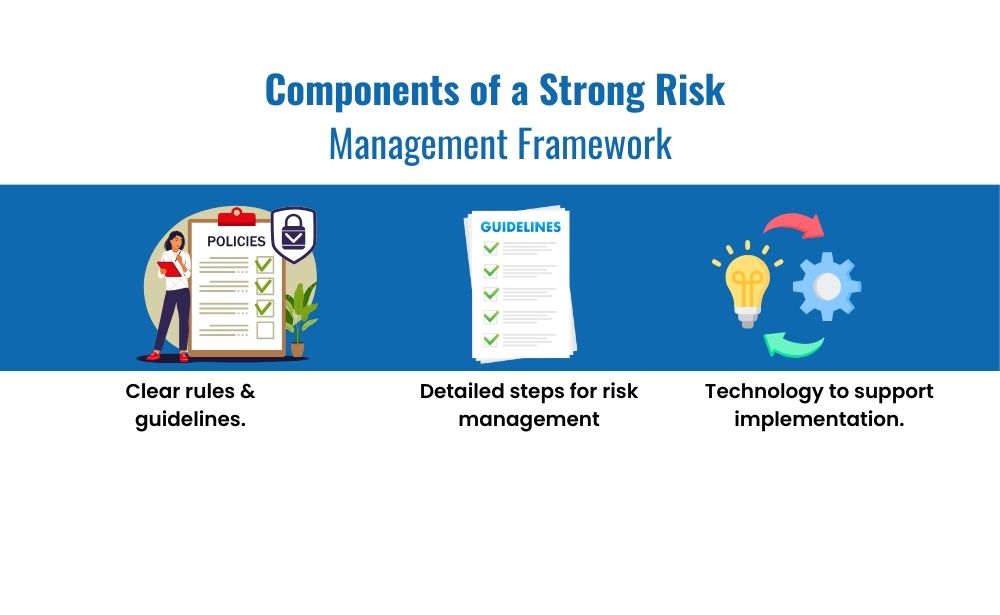
Components of an Effective Risk Management Framework
Now that we’ve identified the risks, what are the components of an effective risk management framework? Essentially, a comprehensive framework encompasses policies, procedures, and tools. Policies outline the rules and guidelines for risk management, ensuring everyone in the organization understands their roles and responsibilities. Procedures detail the step-by-step processes for identifying, assessing, and mitigating risks. Tools, on the other hand, provide the technological support needed to implement these policies and procedures efficiently.
Policies
To begin with, policies set the foundation. They establish the scope of risk management activities and define acceptable levels of risk. These policies must be clear, concise, and communicated effectively across the organization.
Procedures
Subsequently, procedures operationalize these policies. They include risk assessment methodologies, incident response protocols, and regular monitoring practices. Effective procedures ensure that risk management activities are consistent and repeatable.
Tools
Finally, tools play a crucial role. From risk assessment software to incident management systems, these tools streamline processes, enhance accuracy, and provide real-time insights into potential threats.
Software Solutions for Risk Management
Speaking of tools, specialized software solutions can significantly enhance your risk management efforts. But what features should you look for in such software? Firstly, look for comprehensive risk assessment capabilities. Secondly, ensure the software offers robust incident management features. Thirdly, real-time monitoring and reporting are critical. Not only do these features help in promptly identifying and addressing risks, but they also provide valuable data for continuous improvement.
Moreover, the advantages of using specialized software are numerous. These solutions can automate routine tasks, reduce human error, and ensure compliance with industry standards and regulations. Additionally, they provide scalability, allowing your risk management framework to grow with your organization.
Implementation Strategies
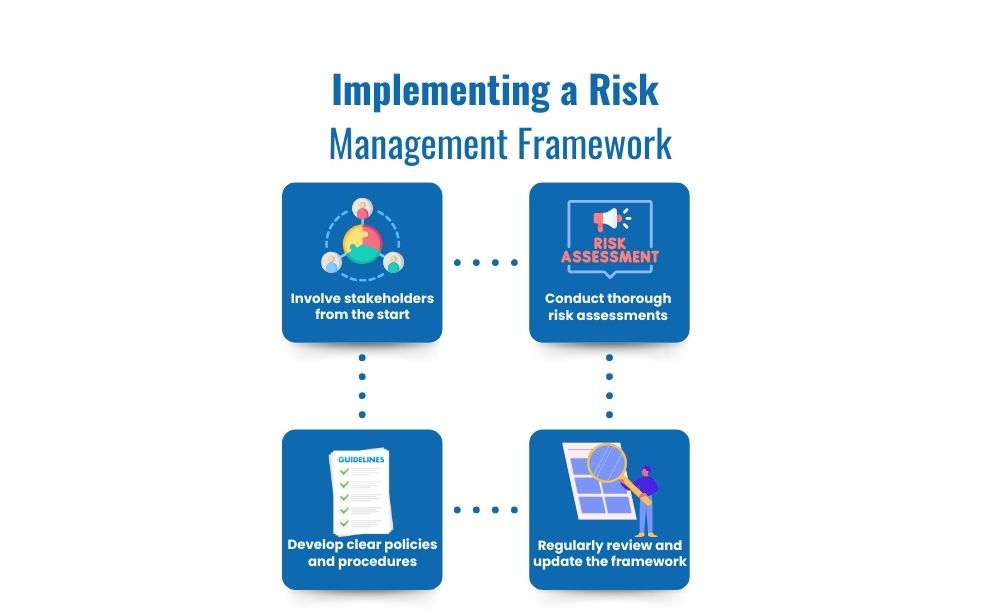
Now, let’s talk about implementation. What are the best practices for developing a risk management framework? Firstly, involve all relevant stakeholders from the start. Their insights and buy-in are crucial for success. Secondly, start with a thorough risk assessment to identify and prioritize risks. Thirdly, develop and document your policies and procedures. Fourthly, invest in the right tools and ensure your team is trained to use them effectively. Lastly, regularly review and update your framework to adapt to new threats and changes in your organization.
Conclusion
In conclusion, the long-term benefits of proactive risk management are undeniable. By building a robust risk management framework for your information systems, you can safeguard your organization’s assets, ensure compliance, and maintain operational continuity. Tools like AsterDocs can support these efforts by providing advanced features for risk assessment and management. So, why wait? Start developing your risk management framework today and stay ahead of potential threats.
By following these steps and incorporating the right tools, you’ll be well on your way to creating a secure, resilient information system that can withstand the ever-evolving landscape of cyber threats.